Microsoft 365 Defender: Threat Explorer - Permissions
Find out what permissions you need in M365 Defender in order to use Threat Explorer for soft/hard delete of emails.
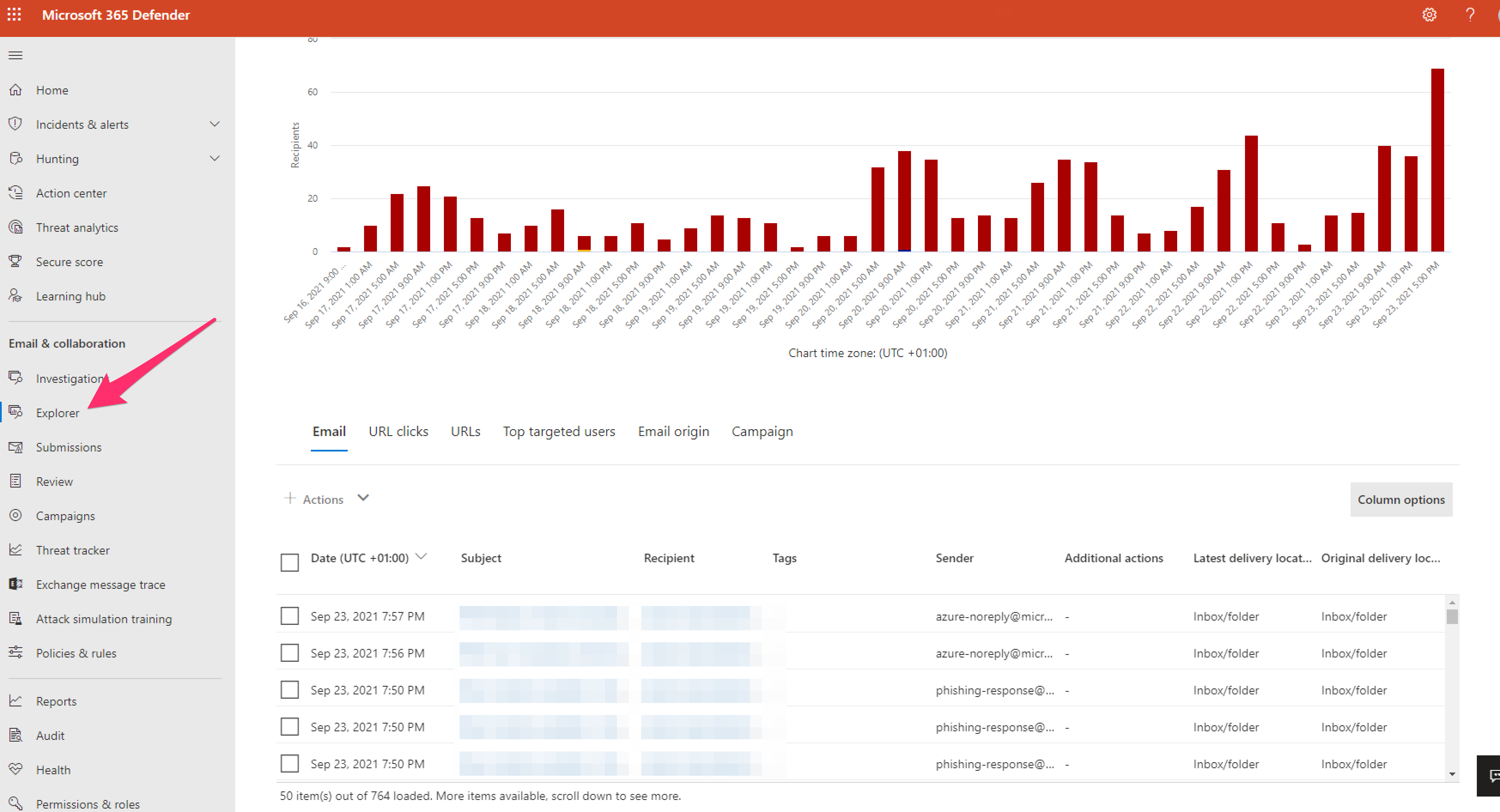
I've had a user want permissions to hard/soft delete emails found to be potentially malicious in M365 Defender Threat Explorer (https://security.microsoft.com/threatexplorer)
What you need to be able to access Threat Explorer in M365:
- Organization Management
- Security Administrator (assign this in the Azure Active Directory admin center (https://aad.portal.azure.com)
- Security Reader (if you PIM upto SecAdmin then you won't need SecReader
Required Licenses
You must have Microsoft Defender for Office 365 to use Explorer or Real-time detections.
- Explorer is included in Defender for Office 365 Plan 2.
- The Real-time detections report is included in Defender for Office 365 Plan 1.
- Plan to assign licenses for all users who should be protected by Defender for Office 365. Explorer and Real-time detections show detection data for licensed users.
Digging into it....
Assign AAD Security Administrator to the user if they don't have it already. It's likely if they are in a SOC or InfoSec that they will probably have this.
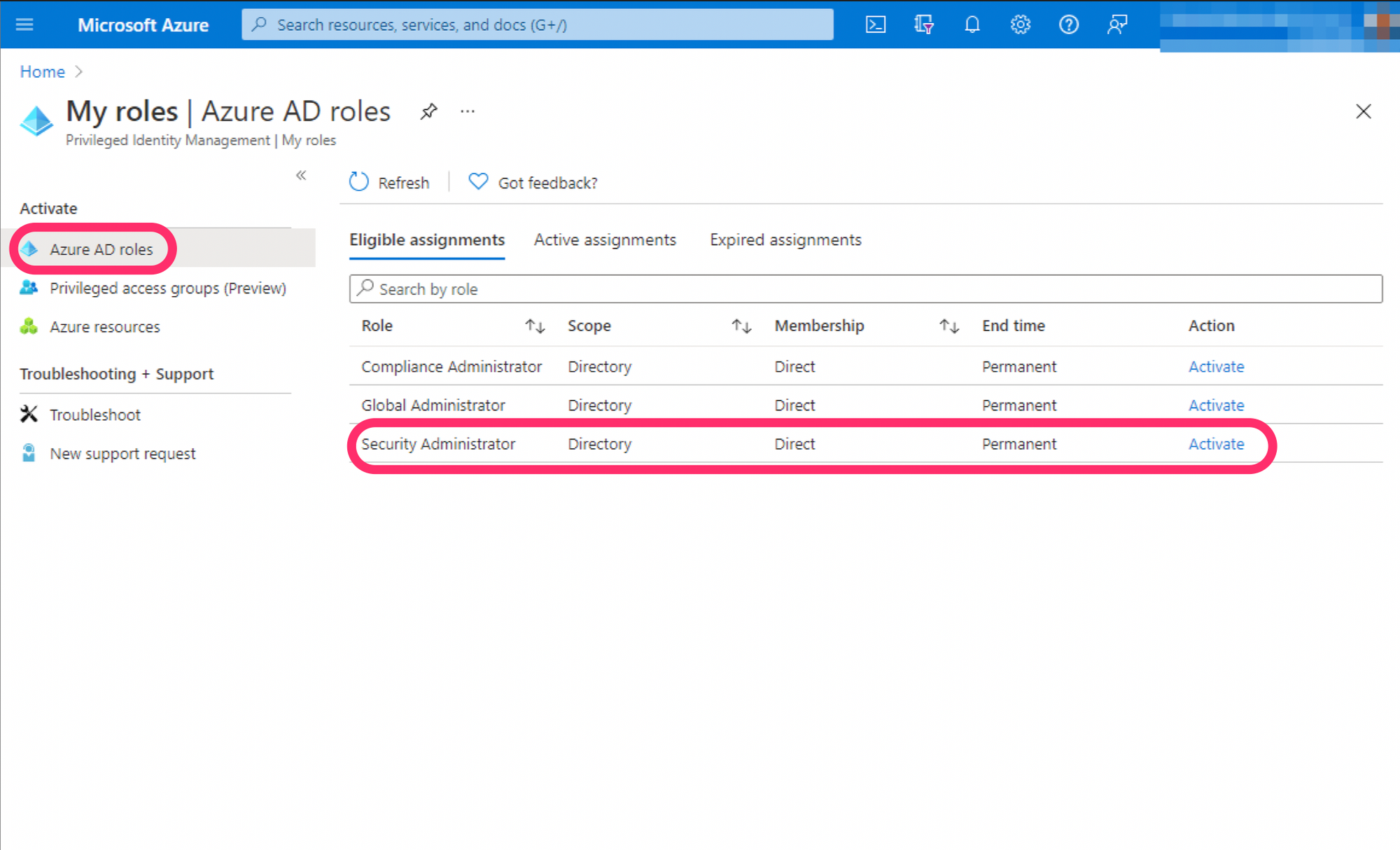
The user was able to access Threat Explorer after pimming up to SecAdmin but couldn't access hard or soft delete.
This delete function was something that I was able to perform but actually couldn't see why I could or where the permission was that enabled me to.
So, let's head over to Permissions & Roles @ https://security.microsoft.com/securitypermissions and select "Roles" under "Email & collaboration roles".
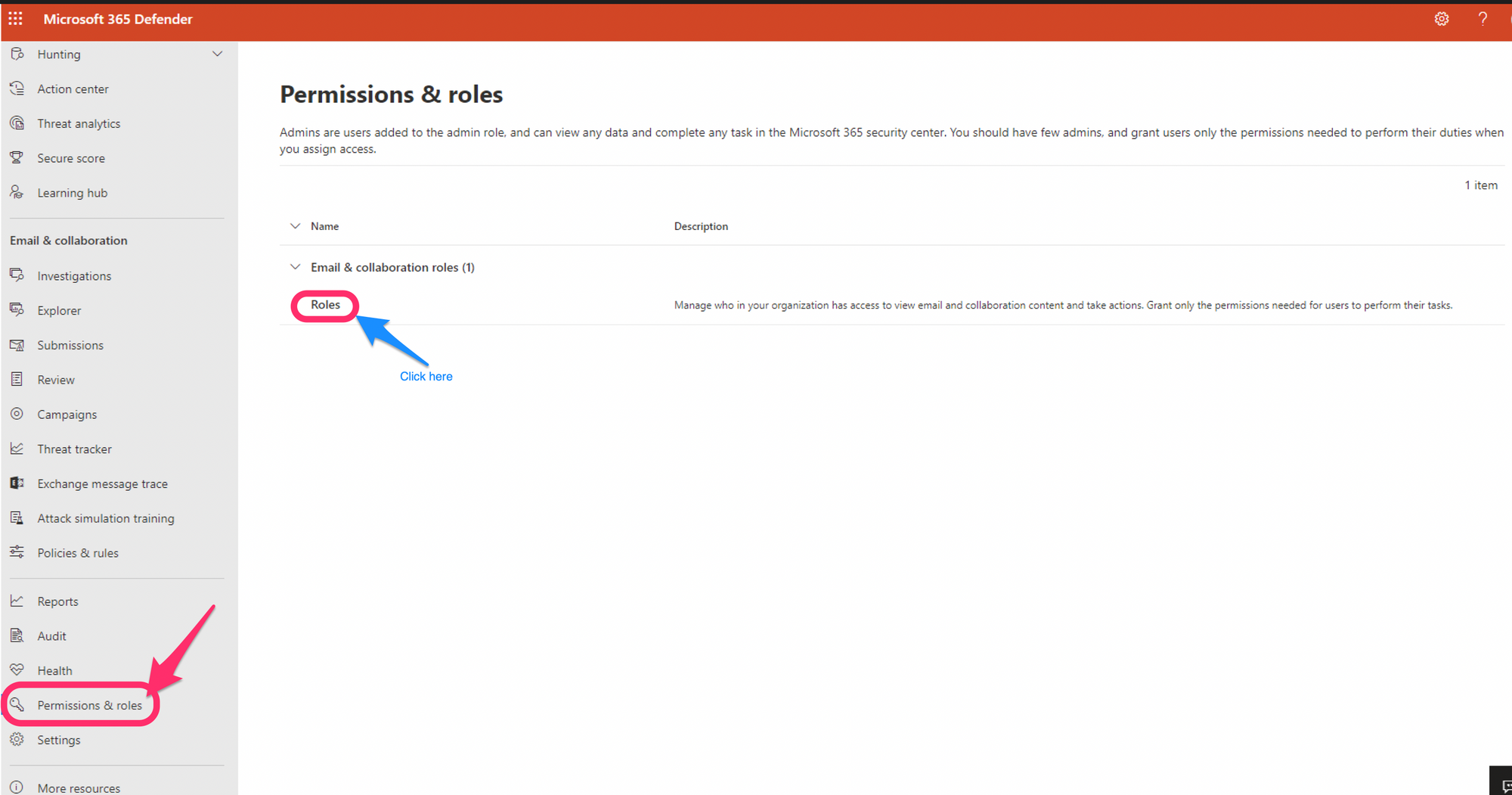
You'll now see a list of roles and permission specific to M365 Defender
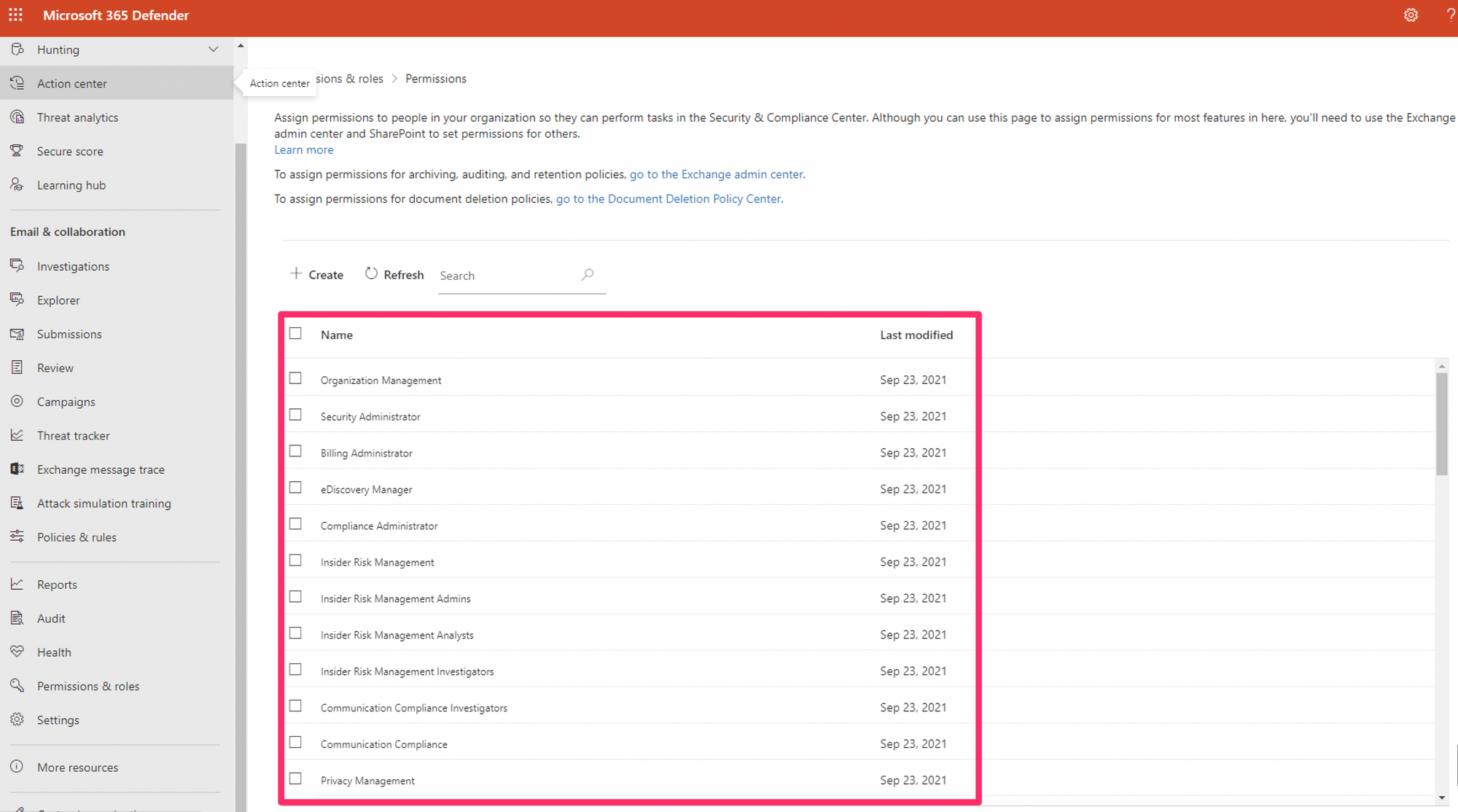
The magic role you need now is "Search & Purge" which appears in "Data Investigator".
The side window will swipe in and you'll see "Search & Purge" under assigned roles.
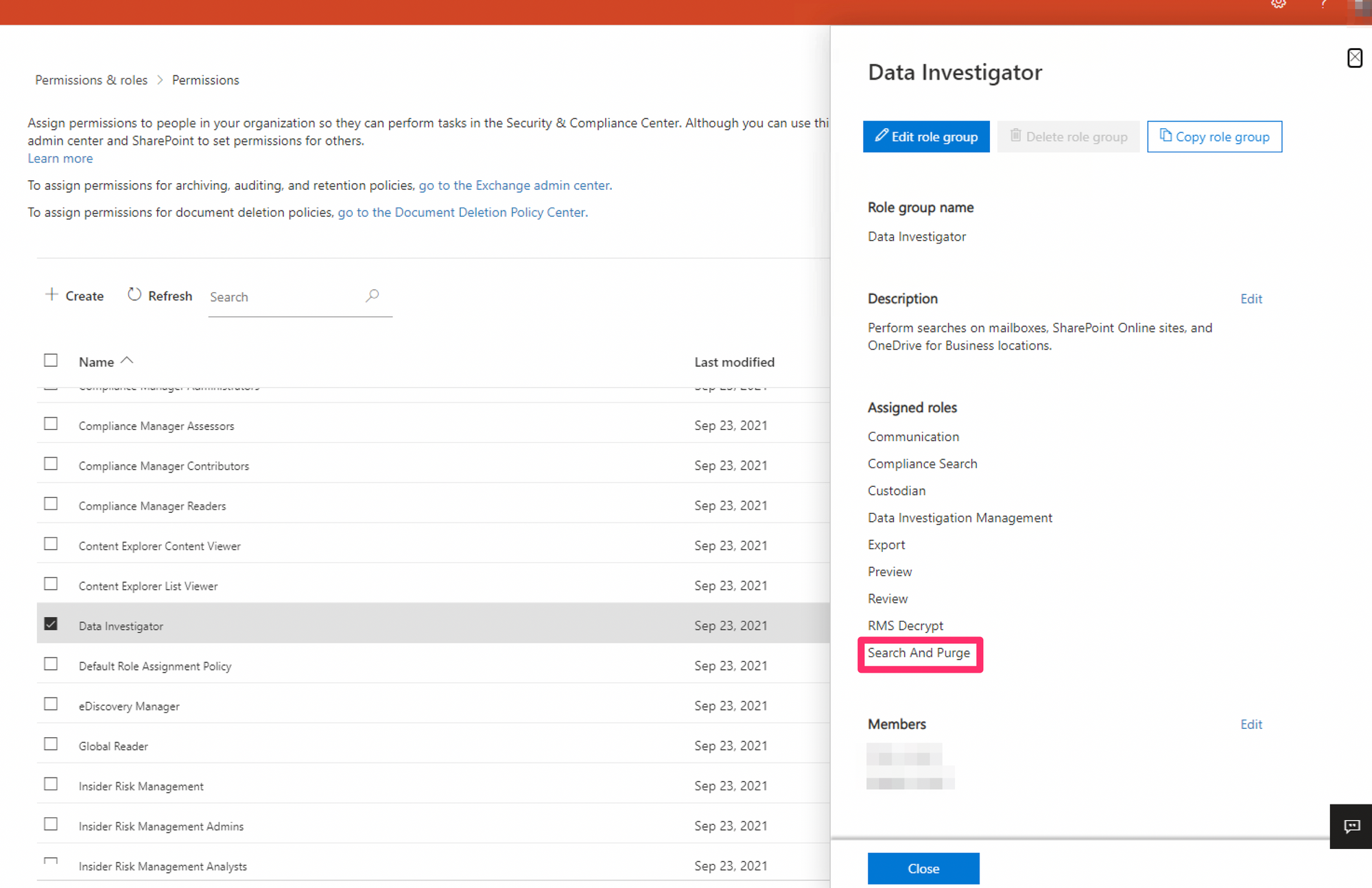
Assign the member to this role then they should be able to purge any emails they look up (making sure they are pimmed upto AAD SecAdmin first).
Granularity within the roles
You really need to be giving users the least privilege and this should actually do the job by giving granularity. Though, there's another role group in M365 that also contains "Search & Purge" and everything else, including the ability to control roles and permissions within M365. This is "Organisation Management" - and very powerful.
Description: Members of this management role group have permissions to manage Exchange objects and their properties in the Exchange organization. Members can also delegate role groups and management roles in the organization. This role group shouldn't be deleted.
Assigned roles:
Audit Logs
Case Management
Compliance Administrator
Compliance Search
Device Management
DLP Compliance Management
Hold
IB Compliance Management
Manage Alerts
Organization Configuration
Quarantine
RecordManagement
Retention Management
Role Management
Search And Purge
Security Administrator
Security Reader
Sensitivity Label Administrator
Sensitivity Label Reader
Service Assurance View
TagContributor
Tag Manager
Tag Reader
View-Only Audit Logs
View-Only Case
View-Only Device Management
View-Only DLP Compliance Management
View-Only IB Compliance Management
View-Only Manage Alerts
View-Only Recipients
View-Only Record Management
View-Only Retention Management
Ideally...
You do not want to be adding too many users to the "Organisation Management" role group in M365 due the power it does possess, but if you need to, then it also contains "Search & Purge"
An alternative to the above, and a lot more secure, would be to create a custom role group here. You can state which roles (such and Search & Purge) you want the users to be able to use. This will introduce granularity and enforce the principle of least privilege.
To summarise...
You need Security Reader as a minimum to even see most things security related, but if you have SecAdmin then that also covers SecReader while providing extra power. You'll then need "Search & Purge" which can either be via the "Data Investigator" role group or the "Organisation Management" role group, which is not recommended if it's only for Search & Purge. Alternatively you can create a custom role group and get even more granularity and really enforce the principle of least privilege.
