Azure Sentinel: Adding Threat Indicators Manually
You can either have an automated Cyber Threat Intelligence feed (STIX/TAXII) or your threat indicators can be added manually in the form of IP, Domain, URL File hash. Let's run through the manual process.

You can either have an automated Cyber Threat Intelligence feed (STIX/TAXII) or your threat indicators can be added manually in the form of IP, Domain, URL File hash. Let's run through the manual process.
Adding your CTI
You'll need to PIM up to Azure Sentinel Contributor role in order to add threat indicators, so do this first.
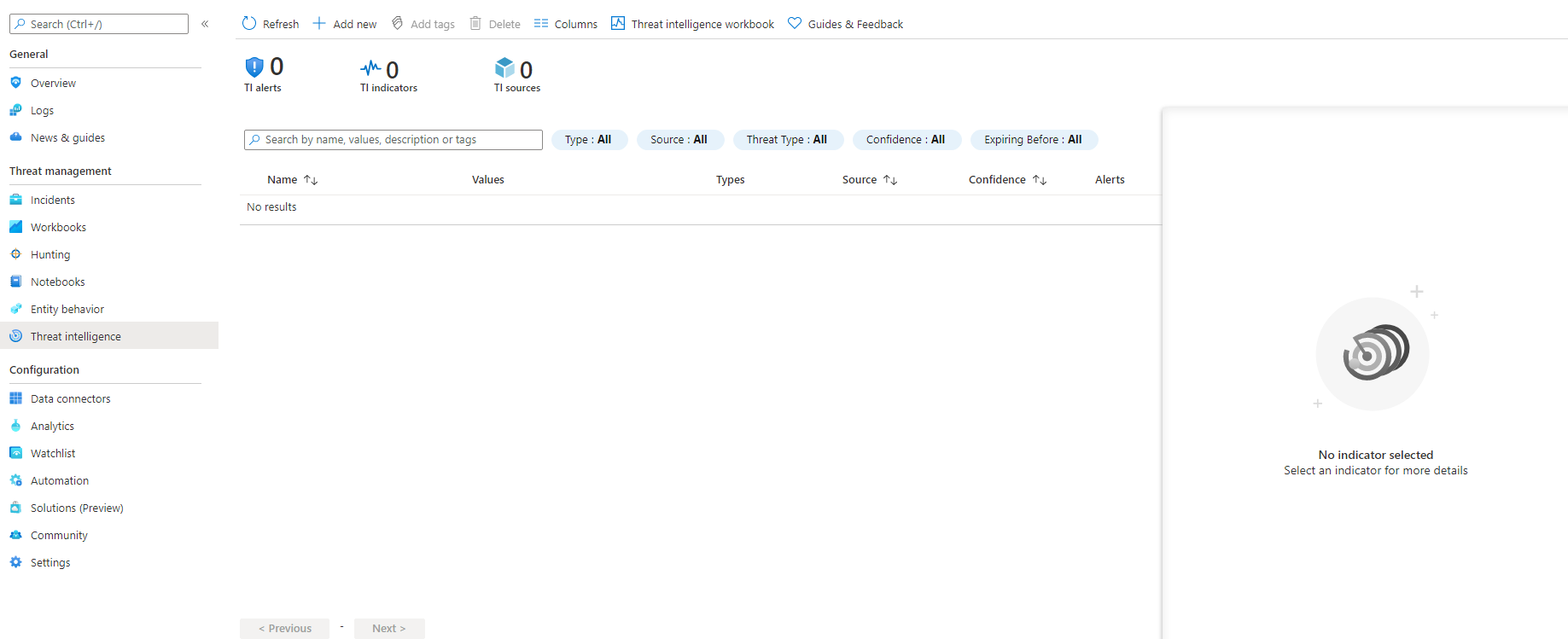
Once you've elevated, head over to the "Threat Intelligence" section in Azure Sentinel and you'll be presented with something that looks like the below (things change often!)
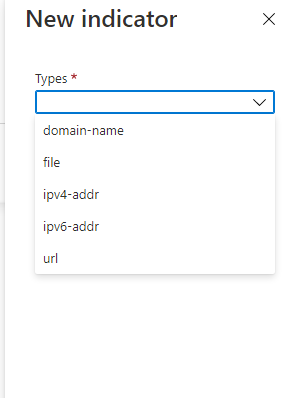
If you've elevated correctly then the "Add new" button will be 'clickable' - select this. A box will swipe in on the right hand side called "New indicator". You can add either domain names, file hashes, IP addresses or URLs.
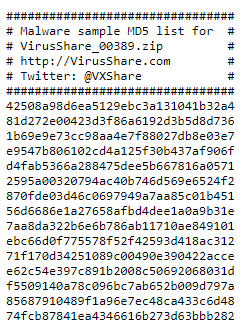
For this demonstration I'll be adding several file hashes, but you can play around and add other indicators following the same process. Select "file" in the types dropdown and then select "Add" under Hashes.
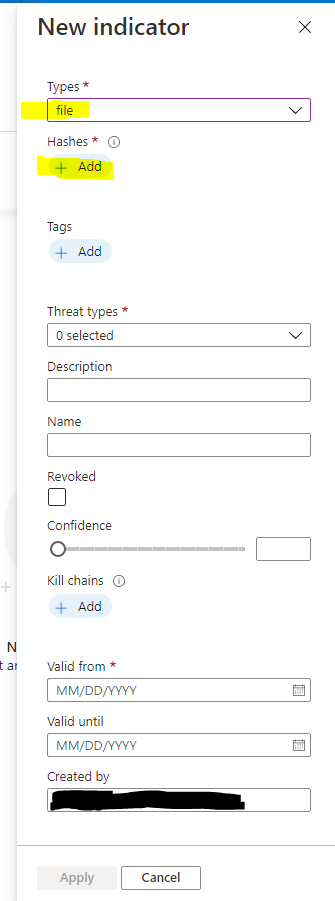
The format will be hashname:Value
I'll be using some genuine MD5 hashes from VirusShare.com for this example.
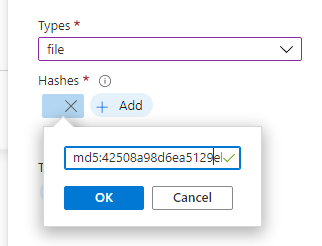
Seeing as they are MD5 hashes, I've added MD5:hashValue as seen below.
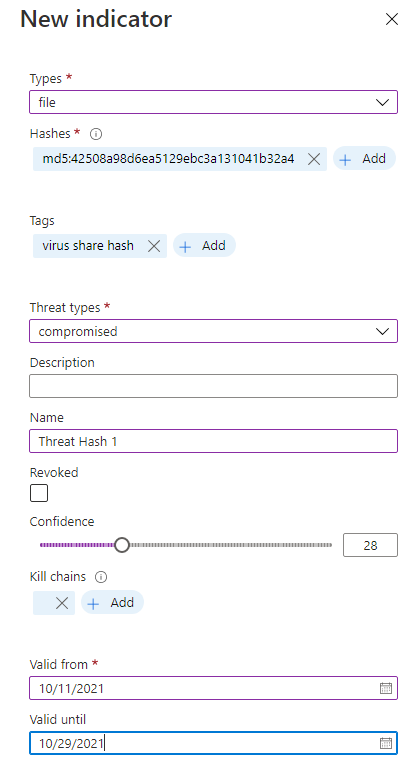
Once the hash has been added, go through and add tags (if you want), choose the threat type, description, name, confidence and a valid through date. Once the indicator hits the valid until date it will be changed to active = false. Select add, then that's it!
All your indicators will be displayed here.
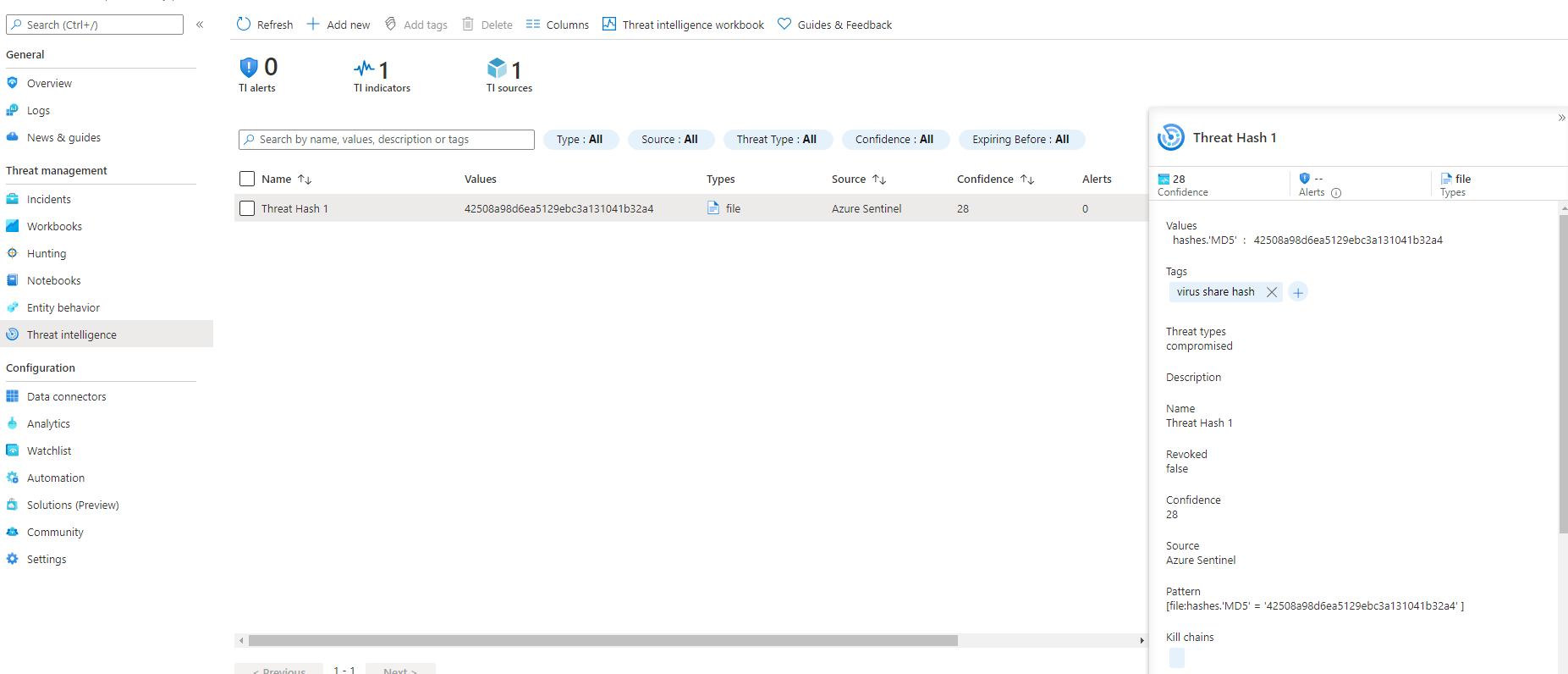
Let's continue to add a few more hashes to the list for this example.
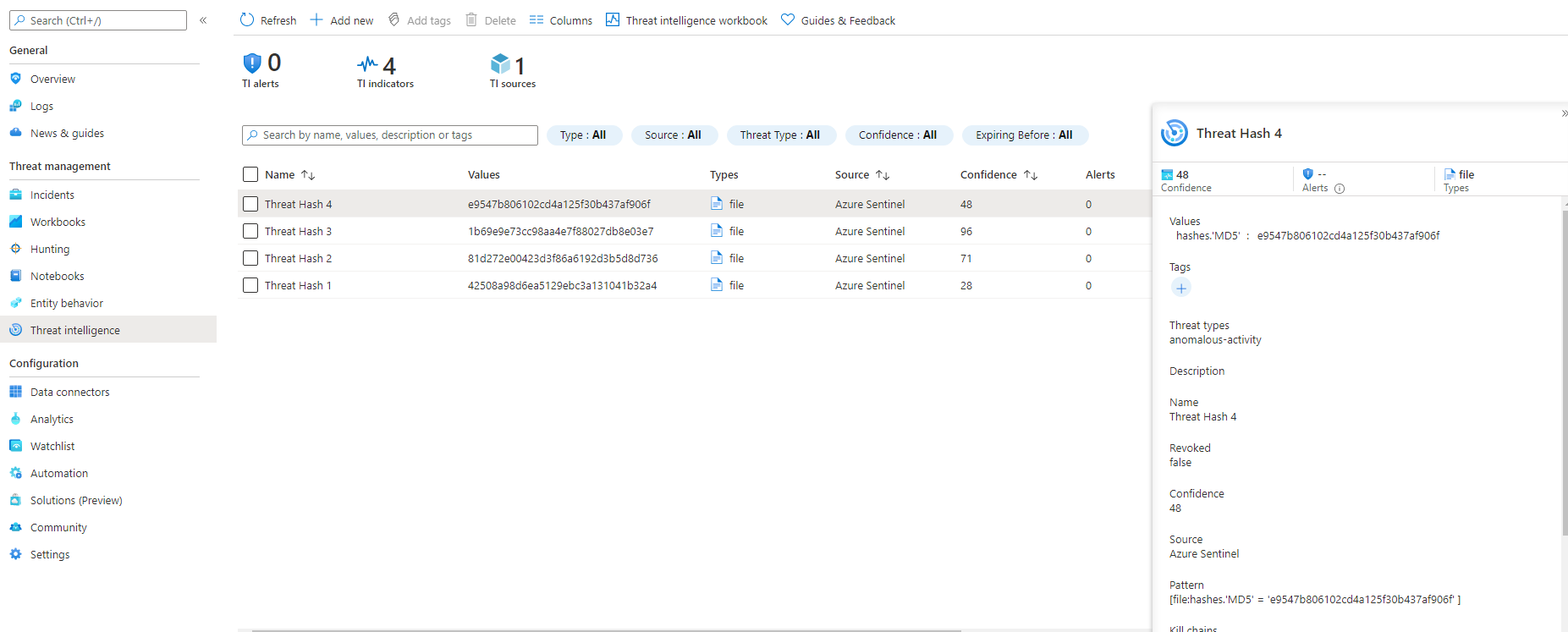
Baring in mind you can't edit these once they've been entered. If you've made a mistake you will have to delete it then add it again. Unfortunately, it doesn't remove it from the ThreatIntelligence table in your Log Analytics Workspace, but it will mark it as active = false.
Check out the post https://cyber.engineer/azure-sentinel-querying-for-your-cyber-threat-indicators/ on how to query your indicators
