Microsoft Defender - Advanced Hunting
Advanced Hunting in 365 is the great starting point for investigating suspicious behavior in your network. The massive range of modules allows it to be very adaptable for a unique environment.

365 has an arsenal of tools available for the ever-favored Microsoft Threat Hunter.
Recently we've had access to the Defender suite and its opened up some more opportunities for analysts to dig deeper with phishing email investigations.
Advanced Hunting in 365 is the great starting point for investigating suspicious behavior in your network. The massive range of modules allows it to be very adaptable for a unique environment. What's great is that it allows for custom detection rules to discover and bring to the surface any potential threats.
This tool uses KQL (Kusto Query Language) as its query language.
Sadly, manual analysis was the only way forward for us in the SOC, requesting the email directly from the user. This is time-consuming, waiting for the email, and can often be left on the back burner for some time.

Users who click these links are often redirected to the attacker's infrastructure. A webpage impersonating a legitimate service convincing enough to get the user to input their credentials and exfiltrate. Sometimes these sites can utilize SSO, populating the user's email address or username, to further leverage the so-called 'legitimacy' of the site.
Advanced hunting will let us look for the quarantined email and download any suspicious attachments that belong to it.
In this article ill cover a few queries I've been playing with.
Email Redirect
The following query will look for any successful Email Redirects in the t-dot format.
EmailUrlInfo
//This regex identifies emails containing the "T-Dot" redirector pattern in the URL
| where Url matches regex @"s?\:\/\/(?:www\.)?t\.(?:[\w\-\.]+\/+)+(?:r|redirect)\/?\?"
//This regex narrows in on emails that contain the known malicious domain pattern in the URL from the most recent campaigns
and Url matches regex @"[a-zA-Z]\-[a-zA-Z]{2}\.(xyz|club|shop)"Malicious File Detect
This is a quick little custom query I wrote when experimenting with the tool at work. This query checks for any hits that Defender will have picked up and blocked, categorized as malware within the last 30 days.
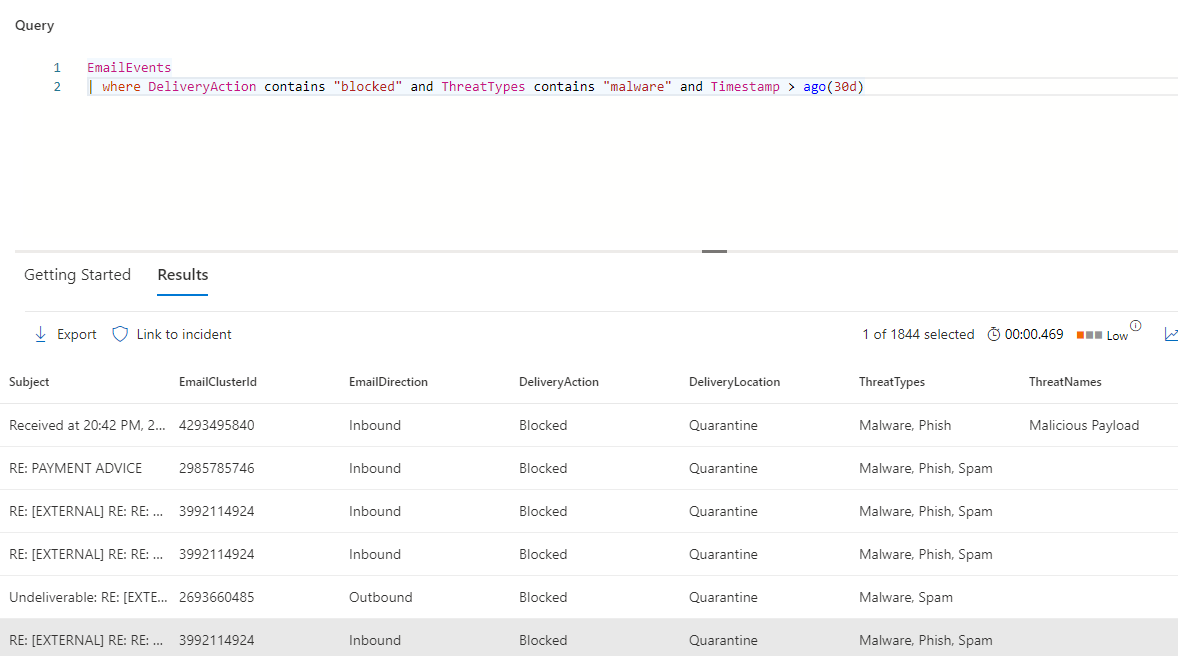
EmailEvents
| where DeliveryAction contains "blocked" and ThreatTypes contains "malware" and Timestamp > ago(30d)Further Reading
Advanced Hunting
Read more about Advanced Hunting's capabilities on the Official Microsoft docs
Advanced Hunting Queries
For more examples and templates for Advanced Hunting queries
